In today’s digital age, cybersecurity is more important than ever. From the apps we use on our phones to the websites we visit and the Wi-Fi networks we connect to, every digital interaction comes with its own set of risks. One critical concept in cybersecurity is the “attack surface.” But what exactly does it mean? And how can we reduce it to stay safe?
Let’s break it down in simple terms.
📌 What is an Attack Surface?
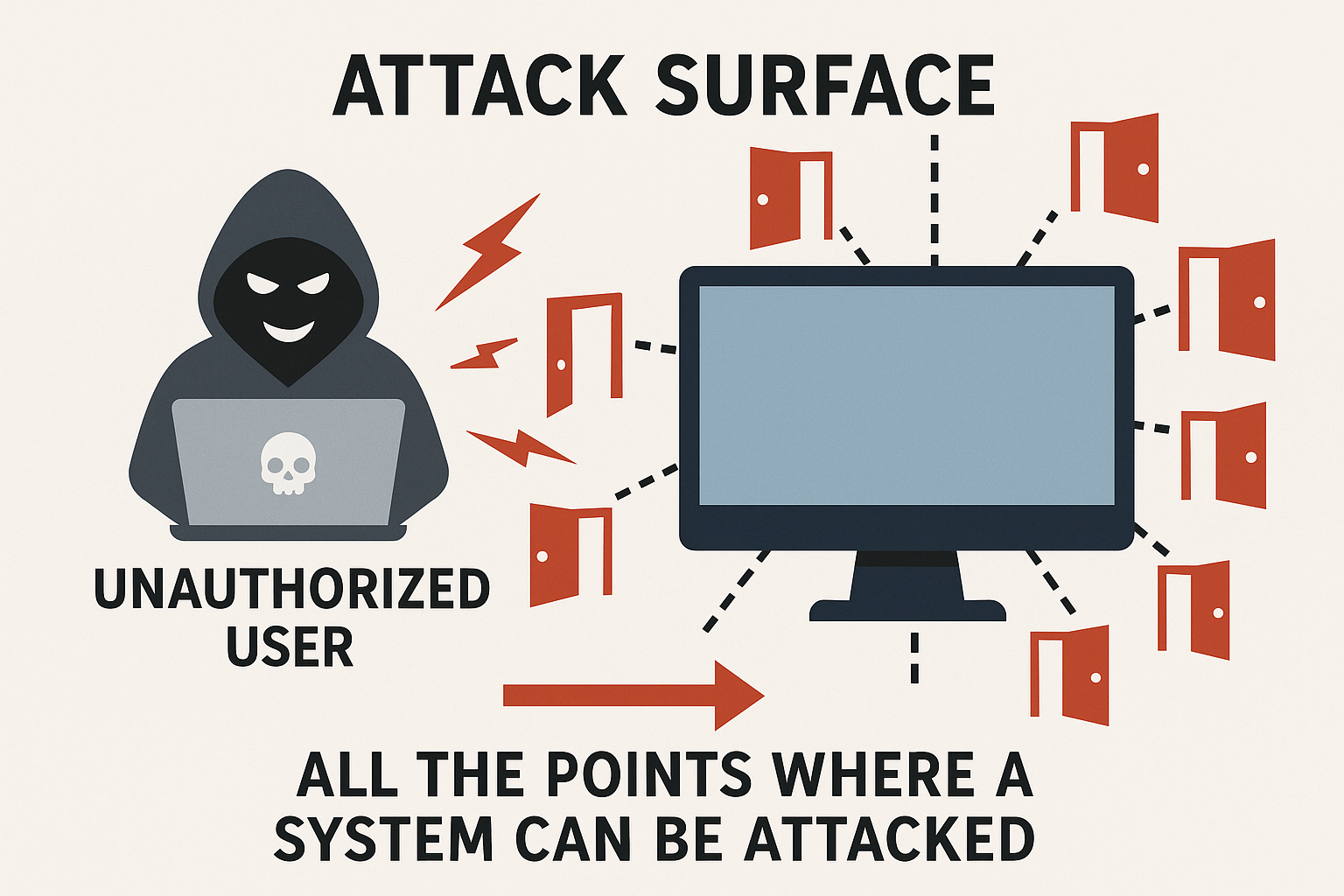
An attack surface refers to all the points in a system where an unauthorized user (like a hacker) could try to enter, extract, or manipulate data. Think of it as the total number of “doors” through which a cybercriminal can attempt an attack.
The larger the attack surface, the more opportunities hackers have to exploit weaknesses. That’s why minimizing the attack surface is a key part of building strong cybersecurity defenses.
🧱 The 3 Main Types of Attack Surfaces
Attack surfaces are typically grouped into three major categories:
1. 🌐 Digital Attack Surface
This includes all the software, networks, applications, servers, APIs, websites, and internet-connected systems that interact with the outside world.
Examples:
- Public-facing web apps
- Open ports
- Cloud storage
- APIs
2. 🖥️ Physical Attack Surface
This refers to physical access points that can be exploited if an attacker gains direct access to your hardware or infrastructure.
Examples:
- USB ports
- Servers and routers
- Laptops, desktops, and removable devices
- Unlocked server rooms
3. 🧑💻 Social Engineering (Human) Attack Surface
This is the most unpredictable attack surface — it includes people. Attackers try to manipulate users into revealing confidential information or giving access through psychological tricks.
Examples:
- Phishing emails
- Fake tech support calls
- Impersonation scams
- Insider threats
🔍 Extended Breakdown of Attack Surfaces
Within those three categories, various components further expose systems. Here’s a breakdown of specific areas often targeted by cybercriminals:
- Network attack surface
- Application/software layer
- Cloud infrastructure
- IoT and smart devices
- Mobile and web apps
⚠️ Common Threats and How to Prevent Them
Here’s a detailed table to help you understand common threats for each type of attack surface and how to protect against them:
| Attack Surface Type | Common Threats | Prevention Measures |
|---|---|---|
| Network Attack Surface | – DDoS attacks – Man-in-the-middle attacks – Packet sniffing | – Use firewalls and IDS/IPS – Enable encryption (TLS/SSL) – Use VPNs for remote access |
| Software/Application Layer | – SQL Injection – Cross-site scripting (XSS) – Zero-day vulnerabilities | – Secure coding practices – Regular patching – Web Application Firewall (WAF) |
| Hardware/Physical Layer | – Unauthorized device access – Tampering – Theft of storage devices | – Physical security (CCTV, locks) – Disk encryption – BIOS-level password protection |
| Human Attack Surface | – Phishing – Social engineering – Insider threats | – Cybersecurity awareness training – Multi-factor authentication – Least privilege access control |
| Cloud Attack Surface | – Misconfiguration – Unauthorized API access – Data leakage | – Proper cloud configuration – Strong IAM policies – Encryption of data in transit and at rest |
| Web & Mobile Apps | – Insecure APIs – Malware injection – Credential stuffing | – API security testing – App security reviews – Strong password policies & rate limiting |
| IoT Devices | – Default credentials – Unpatched firmware – Botnet recruitment | – Change default settings – Regular firmware updates – Network segmentation |
✅ Final Thoughts
Cybersecurity isn’t just a concern for big companies—it’s something every internet user should care about. Understanding attack surfaces helps us better protect our data, devices, and personal information.
The key takeaway?
The smaller your attack surface, the safer your system. So take steps to patch, protect, and prevent. And always stay informed!
